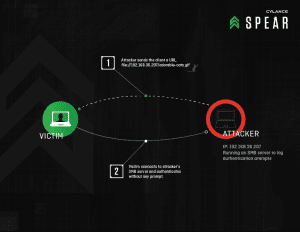
A critical Server Message Block (SMB) #VU672268 in all Windows version including Windows 10 allows potential hackers to steal sensitive login credentialsExamples
Cylance researchers disclosed the vulnerability today on their website in which they said that their study is an extension to a similar research done by Aaron Spangler in 1997. The Redirect to SMB flaw is related to the way that Windows and other software handles some HTTP requests, and researchers say it affects a wide range of applications, including iTunes and Adobe Flash.
The experts at Carnegie Mellon University CERT have given it ID number #VU672268 and warned that once a potential hacker has managed to get the victims credentials, they can easily crack passwords offline. Carnegie Mellon University CERT team have been working with the above said software companies to help them mitigate the issue.
Examples
The Cylance researchers have given following examples show different attacks that could be conducted. In order to effectively demonstrate attack scenarios, the conditions have been simplified. The following are the IP addresses of the computers in the examples: The tools in the examples are as follows: You can download the white paper to get a detailed research about Redirect to SMB attacks. The video of the Proof of Concept is given below :
Microsoft has not commented thus far and a patch can be expected later in the month.