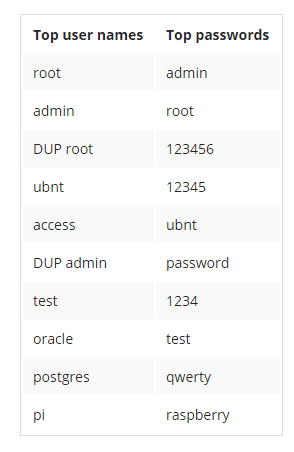
Typically targeting various Linux flavors used to power these devices, IoT malware is seldom seen as danger to the people or companies behind these devices, but everyone else. In the past two years, all IoT malware discovered have been found to be doing the same thing. The infection begins with a cybercriminal or automated service trying to guess thousands of username-password combinations to get into the IoT device’s admin password by using brute-force attacks. Default device passwords help IoT botnets grow Cybercriminals usually get access to the device after a few seconds when the users haven’t changed their device’s default credentials. At this instant, the malware makes changes to the device by adding special code to converse with one of its command and control servers, trapping it into a worldwide botnet, mainly used to execute DDoS attacks, transmit proxy traffic for cybercriminals, and brute-force other IoT devices. In August, Kaspersky had found out that Linux-based botnets had become the most popular DDoS botnets on the market. You will notice someone using an IoT device as a pivot point inside a network only in targeted attacks. But, in general, IoT devices are used as bots for DDoS attacks in most of the cases. This is further made simple by device owners who do not protect their devices with custom passwords. According to Symantec, the table below shows the most encountered passwords in IoT devices worldwide. As one can see from above, many of them are easy guesses and standard passwords for equipment running on Ubuntu, Raspberry Pi platforms or others.
According to Symantec, several IoT malware that are found today comes with cross-platform support, and can target all major IoT hardware platforms such as x86, ARM, MIPS, and MIPSEL platforms. In some cases, there were malware families that went further than these popular platforms and also targeted PowerPC, SuperH and SPARC architectures. Modern IoT malware can spread on its own Attackers using tools like Shodan and automated brute-forcing scripts seldom have to infect IoT devices manually anymore, even though there are cases where this is still required. Latest malware such as the Ubiquiti worm has wormable features that allow it to spread to other devices. IoT malware with self-replication features can help cybercriminals develop huge botnets, some going over 25,000 bots, and in some cases attaining over 120,000 infected devices. There are over one million compromised IoT devices available online, as indicated by Level 3 estimates. In order to launch various types of DDoS attacks on their targets, these botnets are often combined. Brian Krebs, infosec journalist reported a DDoS attack this week that clocked at 620 Gbps after revealing a DDoS-for-Hire service. Early pointers indicate this was the work of a huge botnet of IoT devices, Krebs said. The most popular IoT malware families, according to Symantec are, Linux.Aidra (Linux.Lightaidra), Linux.Ballpit (aka LizardStresser), Linux.Darlloz (aka Zollard), Linux.Dofloo (aka AES.DDoS, Mr. Black), Linux.Gafgyt (aka GayFgt, Bashlite), Linux.Kaiten / Linux.Kaiten.B (aka Tsunami), Linux.LuaBot, Linux.Moose, Linux.Pinscan / Linux.Pinscan.B (aka PNScan), Linux.Routrem (aka Remainten, KTN-Remastered, KTN-RM), Linux.Xorddos (aka XOR.DDos), and Linux.Wifatch (aka Ifwatch). Besides the aforementioned, you can also add Linux.BillGates, Linux.BackDoor.Irc, Mirai, and Rex. The IoT landscape is troubled with unprofessional vendors Several devices are located in the U.S. (28 percent) and China (34 percent), according to the telemetry data. In most cases, the blame usually depends upon one company. For instance, the 25,000-strong botnet mentioned earlier was triggered by a Chinese company that sold white label DVRs, for which it failed to issue a firmware update. The DVRs were bought and sold by 70 other companies, who put their own logo on top. When the users found out that their DVR was not safe and wanted to patch their devices, they couldn’t do so, as their seller was and is still waiting on the Chinese company to fix its errors.