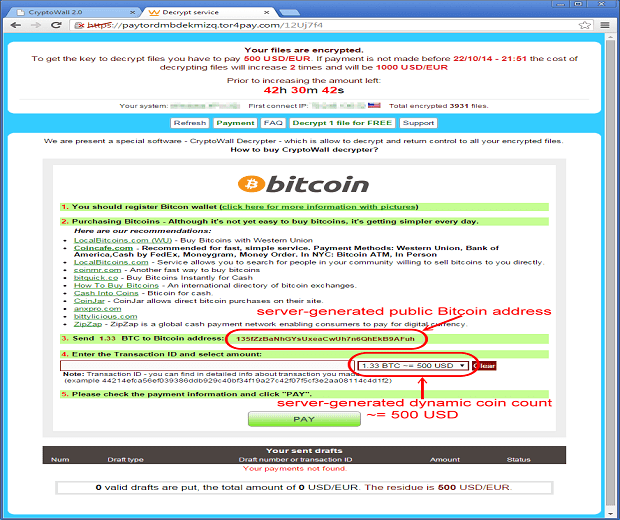
Researchers at proofpoint who reported the malvertising campaign said the malware did not even need a click to get it installed, it automatically get installed using a vulnerability in older version of Flash Players. Once the malware infects the victims computer it encrypts the victims hard drive and asks for a Ransom to be delivered over the internet in exchange for the decryption of the victims files to their original state. More than 3 million visitors per day were potentially exposed to this malvertising campaign which has generated estimated US$25,000 per day for the attackers. List of domains which were affected along with their global Alexa rankings as given on proofpoint blog. The malware in this case, Cryptowall 2.0 Ransomware downloads a Tor client on victim’s machine which it uses to connect to its Command and control (c&c) server and asks for a 500$ equivalent of Bitcoin as ransom.
Proofpoint determined that the impacted websites itself were not infected rather the advertising network on which these websites rely for serving dynamic ads. These dynamic ads in turn were serving the CryptoWall to the the victims. The ads network including OpenX, Rubicon Project and Yahoo Ad Exchange who were unknowingly serving these malicious ads were informed of the malvetising campaigns and as of Saturday proper action was taken to curb the malvertising campaign on these networks.